You're reading the Keybase blog.
There are more posts.
When you're done, you can install Keybase.
Keybase's New Key Model
9/25/2015So far, Keybase has promoted one PGP key per user. You "announce" this key on social media accounts, forming a graph like this:
(1) you hold a private key, and
(2) you have write access on a certain service.
This offers something powerful: username ↔ key conversion, without trusting Keybase. And a transitive bonus: Twitter ↔ GitHub conversion. Glory!
So what's wrong?
While this is a great answer for identity, key management is still dirty.
- as a user, you must get your PGP private key to all your devices
- you're in trouble if you lose a device or fear it has been compromised
- PGP is too complicated for most people
A solution is in the works
The Keybase directory now supports device-specific NaCl keys. From now on, an identity on Keybase can be constructed like this:
she can prove her identity with any key, and the keys are connected
Establishing keys & devices
Soon, Keybase will release open-source apps for:
- iPhone & Android
- OSX, Linux, & Windows (with nice GUIs and CLI)
When you install the Keybase app, it will feel like any other app. Simple. But beneath the hood, it will generate a new key pair. If it's your nth device (n > 1), you will pull out your phone or other device to provision it. A rough-around-the-edges wireframe:
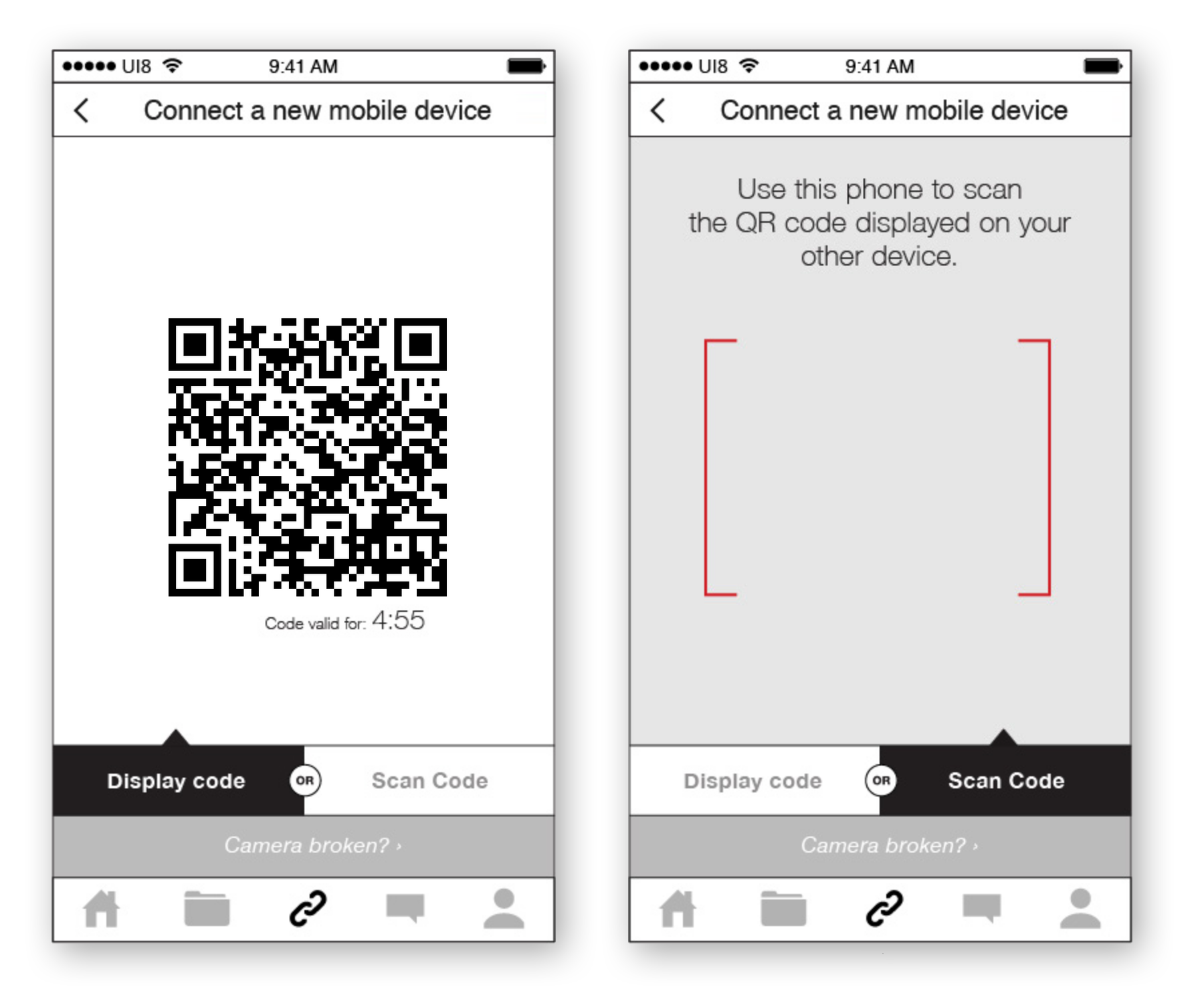
This one-time step will be easy. People are getting used to 2-factor experiences emerging, and we imagine the phone will be the most-used device in provisioning.
Technically, though, this is not a normal 2fa: the devices will share a secret with just each other. They will use that secret to authenticate, sign, & announce each other's keys, including whatever you name each device.
In this way, you can be you, without moving a private key around.
You won't even need a passphrase, and it will take seconds.
Lying by omission?
Provisioning a device key (and choosing a public name for it) is a public action. So are statements of the form "I lost my device." In other words, the Keybase server cannot provide different answers to different users. (Our merkle tree + bitcoin are discussed here. )
Paper keys
Our mobile apps are in active development. Until they're ready, bringing 2 computers together is tough. In the short term, beta testers can now generate paper keys. Slightly cumbersome, these are full NaCl keys that can be used to provision a new computer.
An example:
death punch correct staple battery horse clearly cherry picked words yeah moo car lisp
You can put that in your wallet or stick it in a drawer. In the above example, the first 2 words ("death punch") are a public label, and the rest encodes the private key.
she even used her paper key to provision a device!
the important thing is that she is herself, the sum of all her proofs, on any device
Paper keys, like devices, must be publicly announced and are publicly removed.
Future goals
In the long run, we hope to bring a number of solutions, fully cross-platform:
- safer publishing of signed, unencrypted data (such as source code and binaries)
- safer end-to-end file encryption & sharing (both for your own data, and for your collaborations)
- easier security/identity for other apps that use keys, such as SSH, bitcoin, and other communication apps.
- easier private chatting
That's vague, but we'll have a more specific announcement (especially on 1 and 2) in the next 3-4 months. In the meantime, we're getting all our ducks in a row.
Testing it
Update This new key model is live. If you have a Keybase account and have installed the latest version of Keybase, you'll be asked to make a device key and paper key during first login.
Also, PGP continues to be supported, and, heck, you can now have multiple PGP keys on one account. For the truly bold among us.
Keys for everyone!
- the Keybase team
This is a post on the Keybase blog.
- Keybase joins Zoom
- New Cryptographic Tools on Keybase
- Introducing Keybase bots
- Dealing with Spam on Keybase
- Keybase SSH
- Stellar wallets for all Keybase users
- Keybase ♥'s Mastodon, and how to get your site on Keybase
- Keybase is not softer than TOFU
- Cryptographic coin flipping, now in Keybase
- Keybase exploding messages and forward secrecy
- Keybase is now supported by the Stellar Development Foundation
- New Teams Features
- Keybase launches encrypted git
- Introducing Keybase Teams
- Abrupt Termination of Coinbase Support
- Introducing Keybase Chat
- Keybase chooses Zcash
- Keybase Filesystem Documents
- Keybase raises $10.8M
- The Horror of a 'Secure Golden Key'
- Error Handling in JavaScript