You're reading the Keybase blog.
There are more posts.
When you're done, you can install Keybase.
New Cryptographic Tools on Keybase
❤️ Jan 31, 2020
The Keybase app is getting amazing. It now has everything from an encrypted, free team chat to honest coin flipping. All while becoming more and more usable.
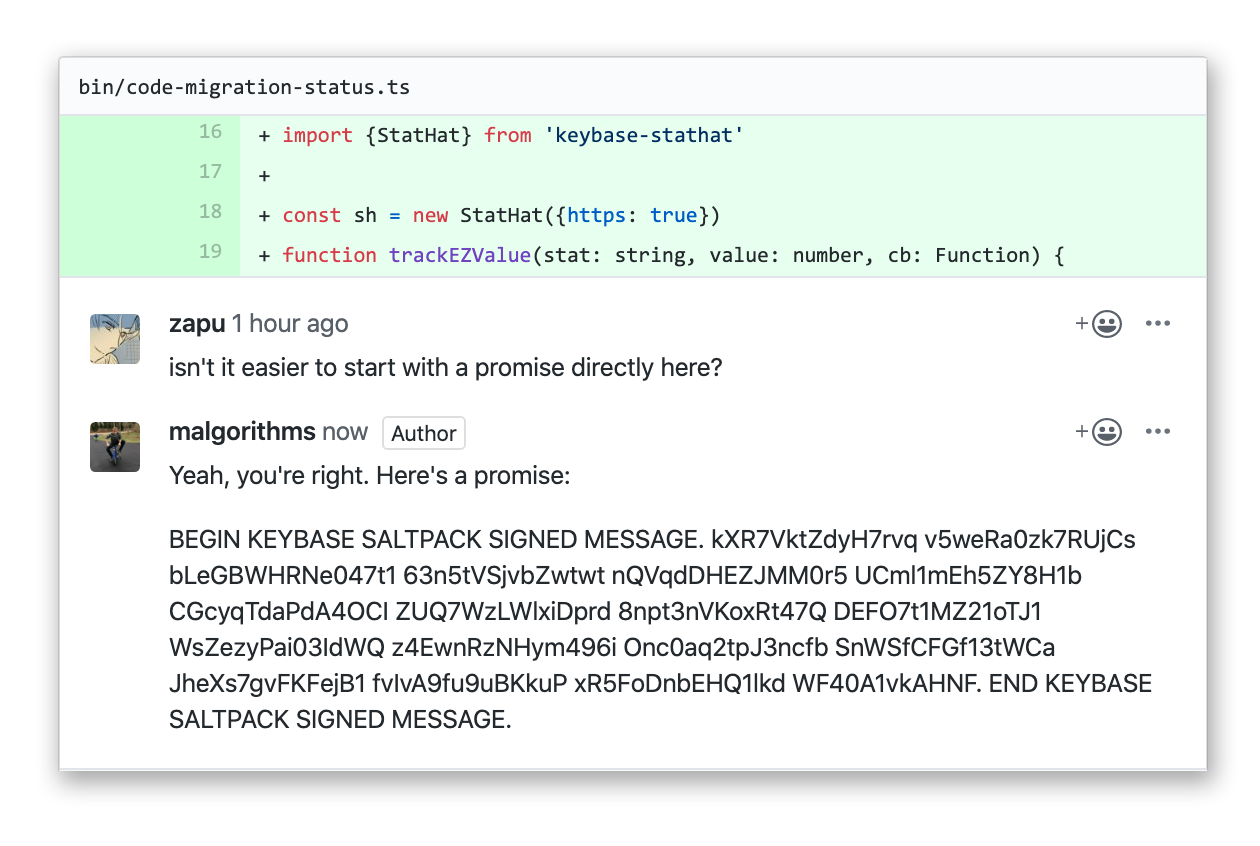
In our pursuit of team collaboration, we've ignored cryptography's core tools. For example, signing a message, and then exporting it, hasn't been possible. The same for encrypting. There has been no way to compose something, transform it, and then paste it into another app or website.
Something like this GitHub exchange I just had:
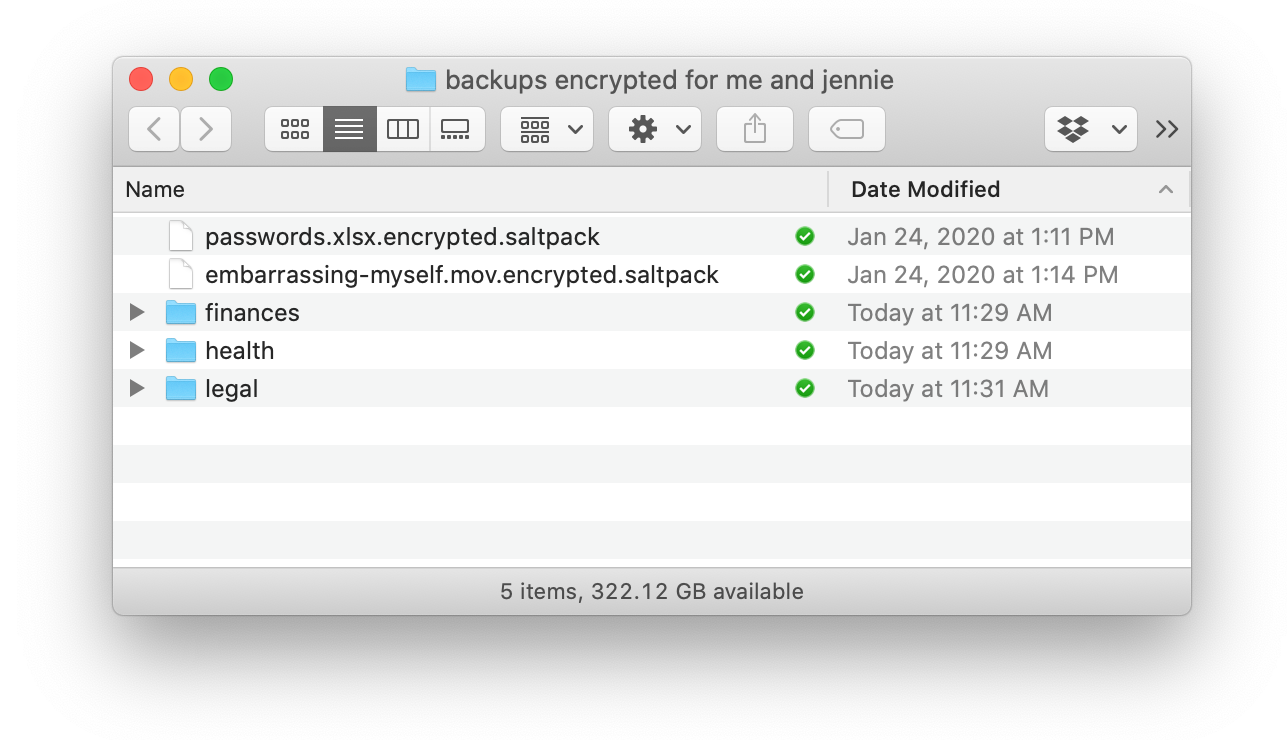
Or these encrypted files I put on a disk:
Well, good news: it's working now. Starting this week, Keybase users can encrypt, decrypt, sign, and verify any text or file, and store or post the output anywhere on the Internet...or in a closet.
See it live
Here is a screen grab of my signing a message.
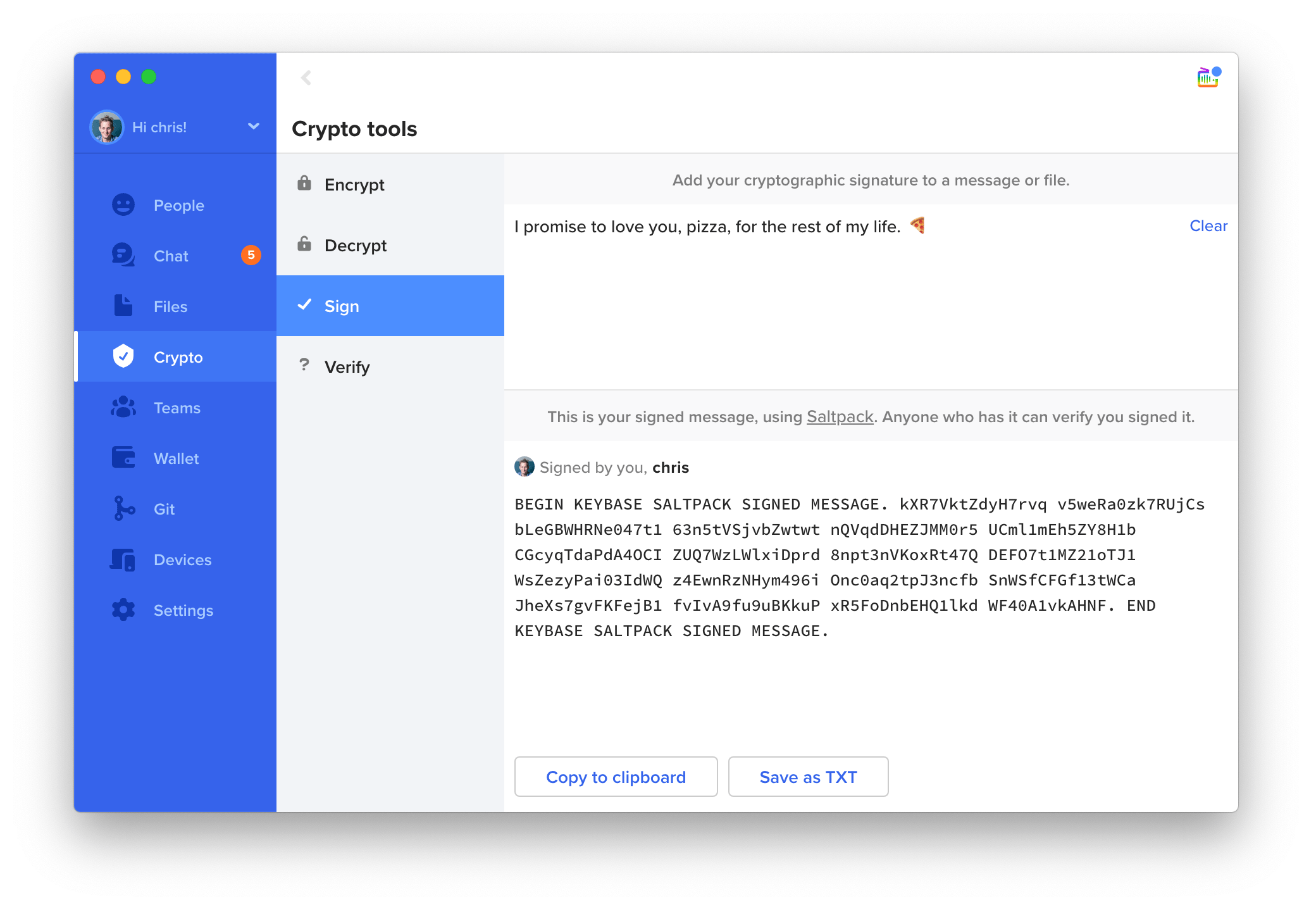
In a few keystrokes, I generated the signed text and copied it to GitHub.
Someone finding my message can check the signature and know it's character-for-character exactly what I signed:
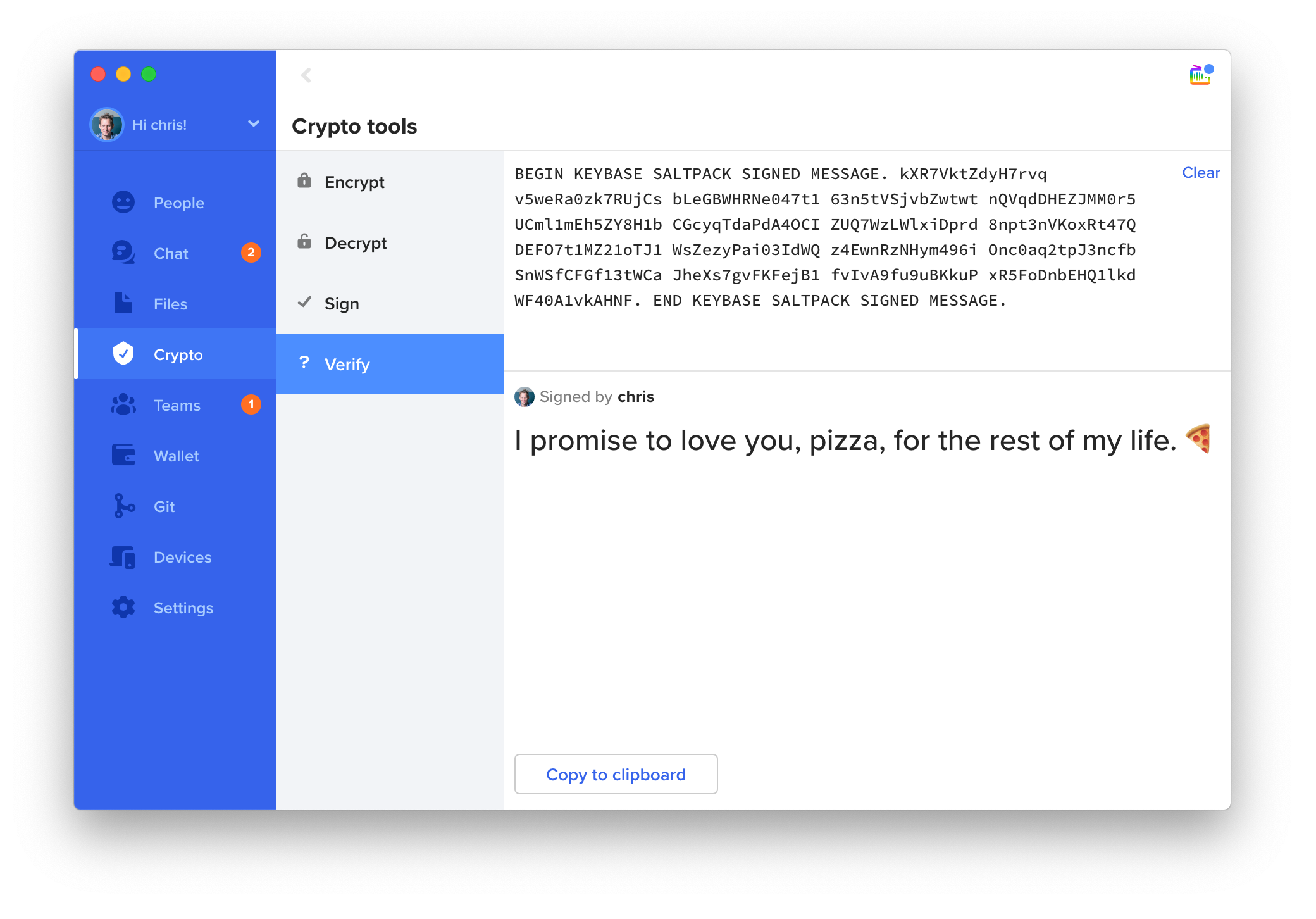
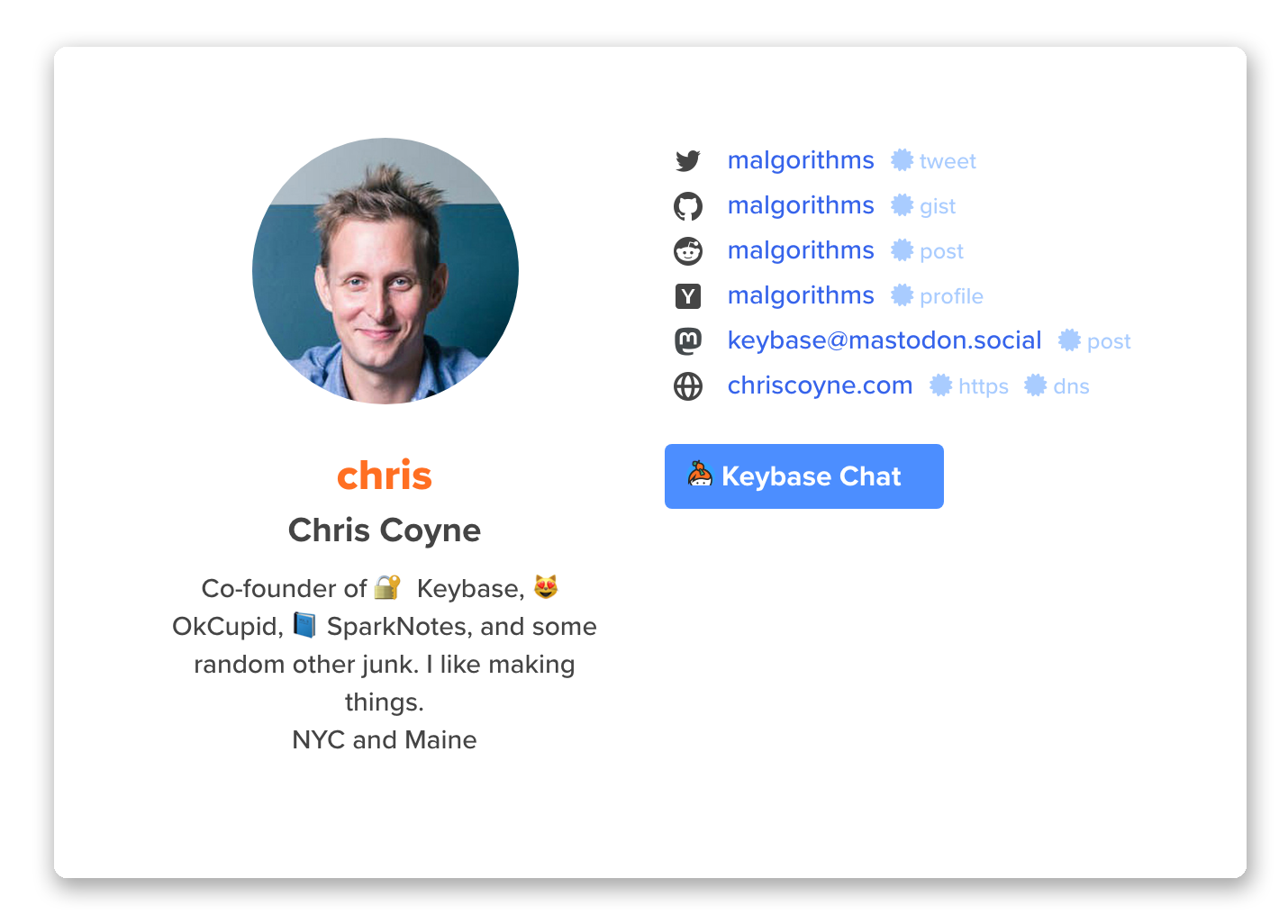
And, if you're unfamiliar with how Keybase works: the reader can tell who I am. I have a long history of owning the Twitter account @malgorithms, the site chriscoyne.com, and so on. This is all verified in the Keybase app without trusting Keybase's horrible, evil servers:
The same goes for encrypting. You can now post encrypted files anywhere you want, even on a public message board or pastebin.
Something magical: future devices

Recall getting a new computer in the olden PGP days. So many confusing details. How do we summon the private key from one device to another? Or shall we make a new key and somehow sign it? How many bits in this new key, we wondered. How high, we asked, must we pin the goat entrails.
With Keybase, you simply bring 2 devices together to provision the new one. Each of your installs gets its own private device key. Your work computer, your home computer, and your phone all have their own keys, which never leave them. They are not backed up to iCloud or Google.
And yet, here's the magic: when you encrypt a file in the Keybase app, it will be available for your—or recipients'—future devices too. The process of adding a device includes a step to ensure this works.
You can safely use Keybase's encryption for backups and similar purposes.
Encrypting for people outside Keybase?!
I just wrote the following message for Twitter user @billieeilish. I simply typed her Twitter handle into the Keybase app and it worked.
BEGIN KEYBASE SALTPACK ENCRYPTED MESSAGE. kiXxI0Cp4MBEQrs K7GWOZokzAqUGLq G3z8DArNvwA9cuG RVJQ4oZ8a6kmgd3 qqpCRVDtcqxZ2HW ZuSRwpJHGly1PV2 UeACoSpQTEhhd8w Sf5K7J1uW4txICM ZXH0S8QgWuOFCev 6vd2DBaUElYOGkw HtDeSrFbcqRsGAk Fa6AAS9EbdnBGB0 M92pqihmApoXGAQ HF0lPlskl91JF3J Q44wooGKAeFs87D lNNsUumFKgr3X1J ADqXdKxmDXPQi2u HWnJ9FCzbLG7LEd oN4E9nUMG2LurUG QPlkgeX3Y14PWb1 ESdmRVboDAxZfzN yuLP9Qpwwkzr0Vu fnuZyGkFr5Y82p3 zUEXZKFaUBEszNQ eKiDwtGtaEepDQ5 6X5CTYP0AShbSZl QB8RHZPbBL1ZZYR MPScK3A2qzdF67n DSohKN3y45vcdbX tTCK4LmjniGQoN1 5LyHNuHIlzX5Ovo mNm2Jfa0tM8GyHV NOs464JZ90rw70M gpwb1JnqIA1uAgS wQahJrPi80HLIVV Pku3rWpnEMKDp5m BC8BpVeP41f3b6N ysxn2S4KWoO5Fjo z9yebEzmdcvhn5p JQvqw708tElqB7p qoe02a3Hfq3i943 bmecQQb1h27bihx hMyYXDIExNOU0cq 1jC3jXCRKChv1O2 fSD2Xaw5JPcOeXZ uzilSlhHWgRtqqD weeBa26EMOQwIn2 eDu6ynC5qAr5ixS GXJ4T822jK2AZbs 6MuH1NgbBFTs8KA JlGkePbMpWXpMaJ 4jZTGvF1kJUtygJ WHBhy9z2PPxO9dT 3OLLZhMNDMU71dO 1T88eWSVJaah5Qx nkMZBlzHVMa5gNA fYg3WTXDdWeIteb L5cDQDFSyRN138H V2QKlEItOiWJ47z IVbWBKqRPTx1iuB 2pw2V7fSS0rlV6m j1kF7E2yRPcShOc sxSySzXEMeK3gVD PrVaVw8RhCkQlO2 8dWzaGaLkeoj9RL 77QD78IyKQp4ekS ZVnhBtghDZqWBqf b9LFzjdkLp6A2Iz CPZTWlbUrW0TD7K YEFb3uh4314nl1i 4Oa7cyAaKjFhX2z FcUomXmCclZs8kP x6AvKhjuUD7LQJD fPFytzrHauHfbOL jyAO7FsFZoMJ6D3 LI2P6lmESsg0Hs8 ztuILDKY5YoKYNM ONje3RnzMcNjHpu ZQUo3SahMGqeFGR XUmvuH0qg7ww4EX uKrO3pwb8Sr4JEr cWkHgmYNpgLat7E ilwQoW038jsawm2 io1NWp2tS7vYPLo rjNu05StOQeLk04 12zlqNAkUzdgk21 GuvUo8l3ZKgpkTe lepVI4yeYRmFnNJ ksVgfegtmcNEyrU 6LB7CMkdJgpANyw Leb2KViZfMxjLPu bPxMrJhrhMBxcVF AepDEV07RCV6XbL xMtWdDBB2mYyPm3 Hhx0m4DR2XPws5E WgvHyBsl39Gu4Nz wGcyvsed594aqYA WiixSR8LhgACJCQ tDJitJYPpaAAEBX 4MFpuCuB5daZkJL Kq1MFYDIDy7Iunj O0myxh6qa66T4eS nJcP63aTZ3nQ8q8 81HZd9ojPMB4gnF VLejO8BQi8fvNog VipjGzC98PSnOZj A0y6R1. END KEYBASE SALTPACK ENCRYPTED MESSAGE.
Despite how public this message is,
it is only readable by me and her.
Billie Eilish is not yet a Keybase user. However, if she joins Keybase and proves her Twitter account, she will be able to decrypt the above. She'll also be able to decrypt this picture that I saved by dropping it onto her Keybase app.
How is this possible? What sick magic is this? Is it server trust? I mean, clearly she doesn't have keys yet.
You can think about it, and I'll answer it in the FAQ below.
Don't forget to install keybase,
🍕Keybase
FAQ
What's with the pizza?
It's the original love triangle
What is Saltpack?
Saltpack (saltpack.org) is a format we published in 2017, being particularly fed up with PGP.
It has a lot of great features for crypto nerds, with none of the complexity or security bugs that have plagued PGP. We also really like how the output looks. You can paste it all over the Web without fear of mangling or bad formatting.
We didn't invent new crypto for it. It's just a combination of existing tools.
Why do you like Keybase's multi-device story so much?
It's safer and easier to understand than PGP. You never need to think about private keys. And on the chat side, it isn't “TOFU” (trust on first use) over and over again, every time someone in your team upgrades their phone.
Anything else you want to say?
Yes:
Not all data is a chat message. “Cryptography” does not mean “secure messenger.”
There's so much more we can do in a world where everyone has keys.
And:
I give up. How does Keybase encrypt for a Twitter, GitHub, or Reddit user?
The app generates a shared key for you and them. Initially, only you hold this key. You then encrypt a message for this key, and you also sign a statement for yourself, an assertion of who else should be allowed to have access to the key.
In my above example, I've signed for myself a statement that I want Twitter user @billieeilish to have access, and I've asked the Keybase servers to let me know when she joins.
When she someday establishes keys, and cryptographically proves her Twitter account, the Keybase servers will ping my apps and ask for me to make available the decryption key to her. My app will check the signed statement from myself, check her tweet, make sure the proof is valid, and then send the decryption keys to her, encrypted for her device keys.
She decrypts the key, gaining access to the file.
Keybase is not a trusted man-in-the-middle here, and no one else has keys. The only weak link here is Twitter: my assertion is like this, in English: “once someone who owns the @billieeilish Twitter account publicly proves a Keybase connection, I'll unlock it.” If Twitter gives that account to someone else or takes control of it, I'll be trusting Twitter's answer. @billieeilish is not yet a human. She's a Twitter account.
Once she has proven the account, we can chat and I'll no longer be trusting Twitter. At that point, I'll have converted the assertion to a chain of signatures.
Tell me more about the multi-device thing
Saltpack has a native notion of multiple devices, allowing you to decrypt data securely on devices you haven't bought yet. This might sound magical. But it's simple: when you provision a new device with an existing device, the old device securely gossips higher level decryption keys to the new device. As long as you have an uninterrupted chain of devices, you retain the ability to decrypt files and texts encrypted in the past. No more, “can you please resend the encryption? I lost my key.”
Is it available in the phone apps?
Not yet—we're working on it. In a release soon.
Does it work from the command line?
Yes.
keybase sign -m "the SHA-2 of app.dmg v1.2.3 is A12354..."
keybase encrypt -m "the club meets @9pm" friend1 friend2 friend3
keybase encrypt -i steamy.mov -o literature-notes.bak friend4
I'd like to do something with Saltpack. Does my project need to talk to Keybase or use Keybase in some way?
No, Saltpack is a general format. We'd love to see its wide adoption.
Are PGP operations available?
Yes, still, from the command line.
# best use
keybase pgp encrypt chris -m 'this is important' > /dev/null
This is a post on the Keybase blog.
- Keybase joins Zoom
- Introducing Keybase bots
- Dealing with Spam on Keybase
- Keybase SSH
- Stellar wallets for all Keybase users
- Keybase ♥'s Mastodon, and how to get your site on Keybase
- Keybase is not softer than TOFU
- Cryptographic coin flipping, now in Keybase
- Keybase exploding messages and forward secrecy
- Keybase is now supported by the Stellar Development Foundation
- New Teams Features
- Keybase launches encrypted git
- Introducing Keybase Teams
- Abrupt Termination of Coinbase Support
- Introducing Keybase Chat
- Keybase chooses Zcash
- Keybase Filesystem Documents
- Keybase's New Key Model
- Keybase raises $10.8M
- The Horror of a 'Secure Golden Key'
- Error Handling in JavaScript